
This article is the first in a multi-part series on information security anti-patterns.
I recall well when I first started out in physical security and the concept of PCI compliance was first introduced. Next to the eBay building was a credit card processing company with many exterior cameras and signage on the door that led me to think they knew what they were doing when it came to security. I asked for a tour and was given one by the facilities manager. I asked him basic questions about access control protocols and was not too surprised to find that all the cameras went back to a DVR locked in a closet behind the receptionist.
Access control lists were not routinely scrubbed as most employees had access to the server room, which was propped open. I asked him about this and he told me that when they know an auditor is coming they secure the door and clean up their logs to be audit ready. I saw many similar dog-and-pony smokescreens at some of the top data centers in the world over a decade of global travels. Which leads us to the first anti-pattern, checkbox compliance.
Definition
Checklist compliance anti-pattern occurs when an organization is seeking to do the bare minimum to pass an audit, get external funding, comply with vendor requirements, or otherwise trying to appease a business requirement.
Why checklist compliance is a bad idea
Unfortunately in today's current global climate there are not only private hackers, but also state-sponsored information security hackers who want nothing more than to exploit your company's prized IP and customer data. Statistics vary greatly depending on the size and type of business of a company being hacked, but most reporting agencies are consistent on one thing: the average cost of a security breach is on the rise. IBM reports that the average cost of a security breach rose from $3.8 million to $4.2 million (USD) in 2021.
When a publicly disclosed breach occurs, investors, customers, employees, and other stakeholders become very interested in what your company has previously done, and plans to do, around security compliance. Companies who fare well through the storm typically are able to show a proactive approach beyond the basics of checkbox compliance to put concerns to rest. Those who attempt to hide negligence – and those who are proved to actually be negligent – do not fare so well and typically CISOs are replaced quickly.
Ransomware is also on the rise and with an average payout of $150,000 in 2021, hackers are motivated financially to be successful. What is likely a much greater cost is the amount of time and money spent to try and postmortem how the information was stolen in the first place and to put remediation into effect to hopefully avoid a reoccurrence in the future.
Common denominators of checkbox compliance anti-pattern
Certainly not an exhaustive list, but common evidence we see of checkbox compliance anti-pattern include:
- "We outsource our payments to a third party, and don't store PII (personally identifiable information) so we don't need to worry about information security."
- Security policies may be in place, but they are outdated and the average employee wouldn't know how to find them, let alone comply with them.
- The person ultimately responsible for security is either a low-level line manager, or there are multiple people sharing the responsibility scattered about and lacking ownership and accountability.
- Security is only a topic of conversation once a year around audit time.
- Security is relegated to a group that hides behind a locked door and requires everyone to submit a ticket and wait in a queue (there is an exclusive anti-pattern coming on this one).
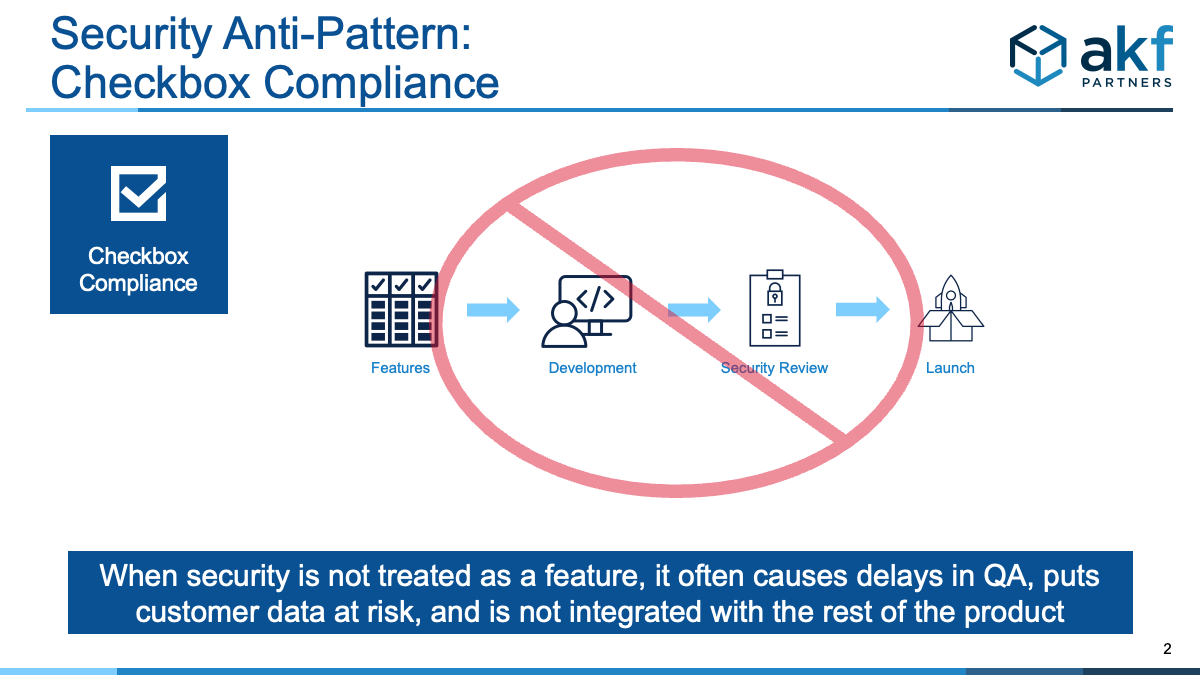
Correct Pattern:
Engineers should:
- Plan for security just as they do features.
- Conduct secure architecture assessment, risk modeling, threat assessment, etc. to inform the backlog.
- Prioritize security in line with other features and not as an afterthought.
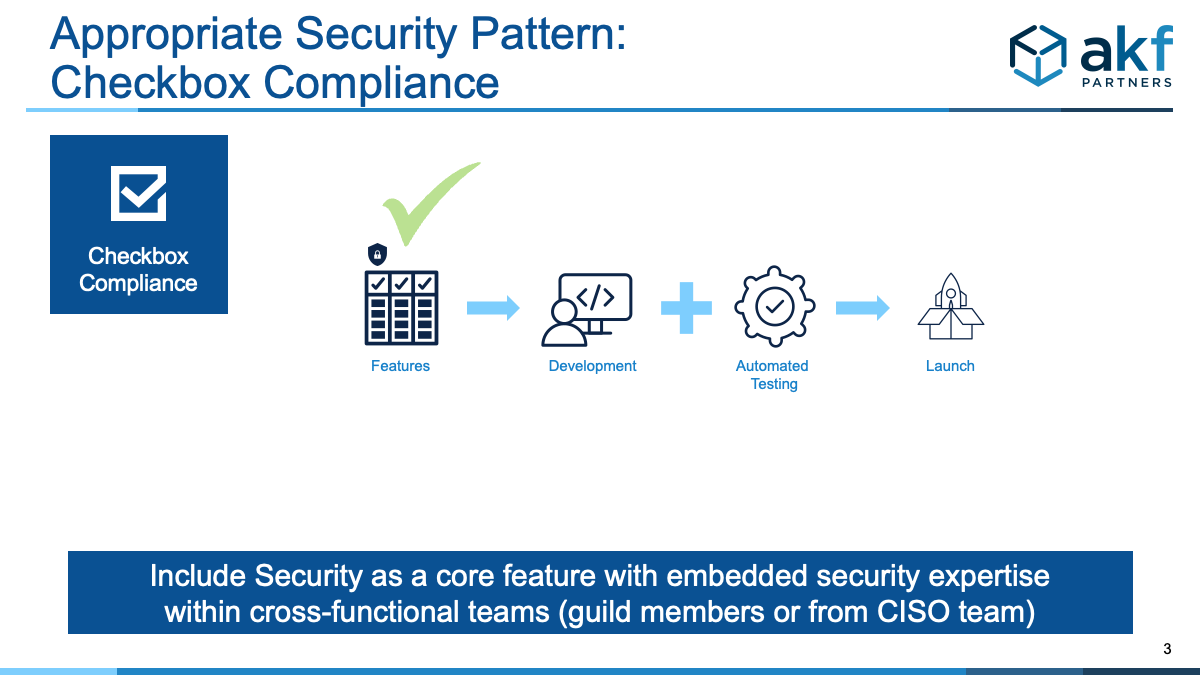
Successful security occurs when it becomes part of the culture. It then organically is a requirement in every development activity resulting in adding value to your products while increasing trust with customers and investors. It becomes part of the DNA of development and delivery. It is also driven by the engineering team - not the security team. The CISO should have representation in the cross-functional team via a guild member or direct team member, but security must be owned by the engineers, not thrown over the wall at the end of the sprint. More on the centralized security anti-pattern in a future post (as a primer, refer to 5 Statements That Should Get CISOs Fired)
Summary
While there is no surefire way to guarantee that you can avoid security breach incidents in the future, going beyond checklist compliance ensures your organization is proactively looking for ways to secure customer and employee information and also helps prepare of future events should they occur.